SHORT CODE: Are special telephone numbers, significant shorter than Full telephone numbers that can be used to address SMS AND MMS messages from mobile phones or fixed phones. They are also known as short numbers. They are new, easy way for media outlets, brand owners and others to use mobile phones to reach and interact with target audience. Short codes are based on text messaging, a service available on almost all digital mobile phones. Instead of a 10-digit number, short code is five or six digit in length, and the digit can
Category Archives: Data Management
Android 5.0 “Key Lime Pie” UI Concepts Hitting the Web, Give Us Very High Hopes
As we approach the rumored date for Android 4.3′s launch on June 20 (at least, that’s what our sources say), many have already come to the realization that we should not expect Google to introduce a new interface for the OS. It will still be called Jelly Bean and nothing too crazy will happen. What most in the business have their money on is that we can expect to see Google change up Android’s look in the iteration after next, being Android 5.0 “Key Lime Pie.” That’s when we will see some new colors, icons, wallpapers, etc. take place.
Graphic designers appear to be already creating their very own concepts for what they would like to see in Android 5.0, playing more with lockscreen widgets and revising the Android homescreen look. Artist Jinesh Shah took to his Google+ page recently to post up a few pictures of his own ideas, some of which we have become big fans of. While it comes off as minimal and clean, there is enough information on any given homescreen and the lockscreen to give off the sense that this concept would be highly functional and practical for users.
The lockscreen widget shows a comprehensive look at this user’s upcoming meeting, even showing a map preview of its location. Below that, we can see upcoming flight details, all of which would be able to be customized under new settings that would come with KLP. As for the homescreen changes, what sets this concept apart from others is the idea of “hidden” widgets. With swipes and other gestures, you could reveal other widgets that don’t necessarily have to be on your homescreen when not being used. It’s a fantastic concept, one that we probably wouldn’t mind seeing implemented.
Share your thoughts on the Android 5.0 concept below!
originally posted on: http://www.droid-life.com/2013/06/14/android-5-0-key-lime-pie-ui-concepts-hitting-the-web-give-us-very-high-hopes/
Sharing your mobile “internet” data connection – free
I will love to say a big “HAPPY NEW YEAR” to all of you that found time to stop by my blog to catch a few tips. I must say that you are the reason I do this and it gives me great pleasure to read your comments, they assure me that we are making good progress. I am just excited that I contribute in my very little way to making your “work and play” a little more fun.
I don’t get to make promises but I trust this year is gonna be a lot more fun and fruitful. Hence, I am continuing from where we left off last year and I am doing this with great respect to our growing need for data (internet data to be precise).
You’ll agree with me that it is becoming more and more expensive to get good internet connections for the increasing number of gadgets ranging from smartphones-to-tablets-to-laptops and even desktops. this has paved the way for proliferation or would I say exploitation by most telephone network providers by providing countless numbers of data packages, all in the bid to cash in on customers pocket content (cash). I however have some pretty good news for y’all. Shhhhhhhhh, don’t tell anybody outside cos I am about to let out some pretty useful secrets for absolutely “FREE”.
Easily Share your mobile data connection
You can share your device’s mobile data connection with a single computer via a USB cable or via Bluetooth: USB tethering or Bluetooth tethering. You can also share your tablet’s data connection with up to eight devices at once, by turning your device into a portable Wi-Fi hotspot. (Not all carriers and tablets support these features.)
When your tablet is sharing its data connection, an icon appears in the Status bar and as an ongoing notification in the Notifications panel (see Managing notifications).
You can also obtain a network connection for your device from a computer via Bluetooth: see Obtain a network connection via Bluetooth tethering.
 |
USB tethering is active |
 |
Bluetooth tethering is active |
 |
Portable Wi-Fi hotspot is active |
 |
Multiple tethering or hotspot connections are active |
For the latest information about tethering and portable hotspots, including supported operating systems and other details, visit android.com/tether.
Share your device’s data connection via USB
If your computer is running Windows 7 or a recent distribution of some flavors of Linux (such as Ubuntu), you typically don’t need to prepare your computer for tethering. But if you’re running an earlier version of Windows or another operating system, you may need to prepare your computer to establish a network connection via USB. For the most current information about which operating systems support USB tethering and how to configure them, visit android.com/tether.
- Use the USB cable that came with your tablet to connect your tablet to your computer.
- Open the Settings application.
- Touch Wireless & networks > Tethering & portable hotspot.
- Check USB tethering.The tablet starts sharing its mobile network data connection with your computer, via USB connection. An ongoing notification icon is added to the System bar, to the left of the time.
- Uncheck USB tethering to stop sharing your data connection. Or just disconnect the USB cable.
Share your device’s data connection via Bluetooth
If your computer can obtain an Internet connection via Bluetooth, you can configure your tablet to share it’s mobile data connection with your computer.
- Pair your tablet with your computer.
- Configure your computer to obtain its network connection via Bluetooth. For more information, see your computer’s documentation.
- Open the Settings application.
- Touch Wireless & networks > Tethering & portable hotspot.
- Check Bluetooth tethering.
Share your device’s data connection as a portable Wi-Fi hotspot
- Open the Settings application.
- Touch Wireless & networks > Tethering & portable hotspot.
- Check Portable Wi-Fi hotspot.
 After a moment, the tablet starts broadcasting its Wi-Fi network name (SSID), so you can connect to it with up to 8 computers or other devices. An ongoing notification is added to the System bar, to the left of the time.
After a moment, the tablet starts broadcasting its Wi-Fi network name (SSID), so you can connect to it with up to 8 computers or other devices. An ongoing notification is added to the System bar, to the left of the time.
When Portable Wi-Fi hotspot is checked, you can change its network name or secure it. See Rename or secure your portable hotspot.
Uncheck Portable Wi-Fi hotspot to stop sharing your data connection via Wi-Fi.
Rename or secure your portable hotspot
You can change the name of your tablet’s Wi-Fi network name (SSID) and secure its Wi-Fi network.
- Open the Settings application.
- Touch Wireless & networks > Tethering & portable hotspot.
- Ensure Portable Wi-Fi hotspot is checked.
- Touch Portable Wi-Fi hotspot settings.
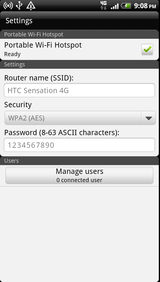
- Touch Configure Wi-Fi hotspot.
The Configure Wi-Fi hotspot dialog opens.
You can change the network SSID (name) that other computers see when scanning for Wi-Fi networks.
You can also touch the Security menu to configure the network with Wi-Fi Protected Access 2 (WPA2) security, with a preshared key (PSK).
If you touch the WPA2 PSK security option, a password field is added to the Configure Wi-Fi hotspot dialog. If you enter a password, you will need to enter that password when you connect to the tablet’s hotspot with a computer or other device. Or touch Open in the Security menu to remove security from your Wi-Fi network.
- Touch Save.
Voilà….Enjoy.
Adamu Fun Bala CSA; MD/CEO Lynxx Systems & Communication Technology LTD; 08035158065
Cloud Computing Architecture
When talking about a cloud computing system, it’s helpful to divide it into two sections: the front endand the back end. They connect to each other through a network, usually the internet. The front end is the side the computer user, or client, sees. The back end is the “cloud” section of the system.
The front end includes the client’s computer (or computer network) and the application required to access the cloud computing system. Not all cloud computing systems have the same user interface. Services like Web-based e-mail programs leverage existing Web browsers like Internet Explorer or Firefox. Other systems have unique applications that provide network access to clients.
On the back end of the system are the various computers, servers and data storage systems that create the “cloud” of computing services. In theory, a cloud computing system could include practically any computer program you can imagine, from data processing to video games. Usually, each application will have its own dedicated server.
A central server administers the system, monitoring traffic and client demands to ensure everything runs smoothly. It follows a set of rules called protocols and uses a special kind of software called middleware. Middleware allows networked computers to communicate with each other. Most of the time, servers don’t run at full capacity. That means there’s unused processing power going to waste. It’s possible to fool a physical server into thinking it’s actually multiple servers, each running with its own independent operating system. The technique is called server virtualization. By maximizing the output of individual servers, server virtualization reduces the need for more physical machines.
If a cloud computing company has a lot of clients, there’s likely to be a high demand for a lot of storage space. Some companies require hundreds of digital storage devices. Cloud computing systems need at least twice the number of storage devices it requires to keep all its clients’ information stored. That’s because these devices, like all computers, occasionally break down. A cloud computing system must make a copy of all its clients’ information and store it on other devices. The copies enable the central server to access backup machines to retrieve data that otherwise would be unreachable. Making copies of data as a backup is called redundancy
The Clouds are Gathering (about cloud computing)
 You probably have heard this term a number of times and have wondered what it could mean. What? Cloud computing? It is interesting to know that this has been around for some time now, but all thanks to a number of concerns/fears. However, it seems to be set to explode and transform the IT industry. For good? this is left to be seen. Now let’s say you’re an executive at a large corporation. Your particular responsibilities include making sure that all of your employees have the right hardware and software they need to do their jobs. Buying computers for everyone isn’t enough — you also have to purchase software or software licenses to give employees the tools they require. Whenever you have a new hire, you have to buy more software or make sure your current software license allows another user. It’s so stressful that you find it difficult to go to sleep on your huge pile of money every night.
You probably have heard this term a number of times and have wondered what it could mean. What? Cloud computing? It is interesting to know that this has been around for some time now, but all thanks to a number of concerns/fears. However, it seems to be set to explode and transform the IT industry. For good? this is left to be seen. Now let’s say you’re an executive at a large corporation. Your particular responsibilities include making sure that all of your employees have the right hardware and software they need to do their jobs. Buying computers for everyone isn’t enough — you also have to purchase software or software licenses to give employees the tools they require. Whenever you have a new hire, you have to buy more software or make sure your current software license allows another user. It’s so stressful that you find it difficult to go to sleep on your huge pile of money every night.
Soon, there may be an alternative for executives like you. Instead of installing a suite of software for each computer, you’d only have to load one application. That application would allow workers to log into a Web-based service which hosts all the programs the user would need for his or her job. Remote machines owned by another company would run everything from e-mail to word processing to complex data analysis programs. It’s called cloud computing, and it could change the entire computer industry.
In a cloud computing system, there’s a significant workload shift. Local computers no longer have to do all the heavy lifting when it comes to running applications. The network of computers that make up the cloud handles them instead. Hardware and software demands on the user’s side decrease. The only thing the user’s computer needs to be able to run is the cloud computing system’s interface software, which can be as simple as a Web browser, and the cloud’s network takes care of the rest.
There’s a good chance you’ve already used some form of cloud computing. If you have an e-mail account with a Web-based e-mail service like Hotmail, Yahoo! Mail or Gmail, then you’ve had some experience with cloud computing. Instead of running an e-mail program on your computer, you log in to a Web e-mail account remotely. The software and storage for your account doesn’t exist on your computer — it’s on the service’s computer cloud.
What makes up a cloud computing system? Find out in the next Post.
Do Yourself a Favor – Make a Backup
Information Technology has become part of our daily lives, we have become so used to it that we often times feel incomplete if some of our gadgets are not in our possession for one reason or another (laptops, Phones, etc). I can say that we have seamlessly infused them into our lives.
However, with technology comes responsibility, we have all been affected by what I call an undesirable occurrence. It happens even more often than we expect or even desire, yet we don’t take steps or develop strategies to mitigate it. It is called “Data Disaster/Loss”.
 This happens on any electronic data processing device of any sort. The bad news is that, it is normal, it must occur one way or another. I have had a number of instances where a friend’s laptop is stolen and in so much pain I hear them say something like “If they could only bring back my hard disk”. This suggests that they have had very important data stored in there, but have now been thrown off tangent because they’ve got no way/where to retrieve these data. It is indeed heart breaking. There are still worst scenarios where another man’s life depends on the said data. The good news is that you can prepared against the evil day.
This happens on any electronic data processing device of any sort. The bad news is that, it is normal, it must occur one way or another. I have had a number of instances where a friend’s laptop is stolen and in so much pain I hear them say something like “If they could only bring back my hard disk”. This suggests that they have had very important data stored in there, but have now been thrown off tangent because they’ve got no way/where to retrieve these data. It is indeed heart breaking. There are still worst scenarios where another man’s life depends on the said data. The good news is that you can prepared against the evil day.
Any document, database, website, application, statistics, spreadsheet, or other types of files are at risk of being permanently lost if it exists in only one location. Hard drive malfunction and computer viruses, as well as things like fire, human error and even sabotage can and do happen to computer systems. When these problems occur, weeks or months of work can disappear in an instant, lost forever. The best protection from such a disaster is to have multiple versions of the data, including at least one copy stored in an alternate location. This is the basic principle behind all backup strategies.
Many businesses have a backup procedure already in place. However, they may not be aware of the alternatives to their current expensive, manual, archaic, tape-based backup processes. With business operations so reliant on information technology, it is vitally important to identify alternatives that can eliminate vulnerabilities. In addition, it is important to utilize an effective data protection service that will allow you to quickly restore business operations.
Cases in View
- More recently the second floor of the Secretariat of the Institute of Chartered Accountants of Nigeria was affected by fire in the early hours of Saturday, September 26, 2009. Initial report from the Security Guards on duty, revealed that the fire started at about 1.25 am following the restoration of electricity supply by Power Holding Company of Nigeria (PHCN) after a period of power outage. The fire was restricted to the second floor due to the timely intervention of the Federal and Lagos State Fire Services, as well as Fire Service Units of some corporate organisations like Union Bank Plc. and Eko Hotel and Suites for which the Institute is immensely grateful.
The offices affected were: Research and Technical Directorate, Computer room, Director, Membership Affairs and Corporate Affairs. I leave you to ponder on the amount of data that was lost.
- In 2007 the offices of the National Agency For Drug Administration and Control (NAFDAC) in Kaduna and Lagos were both gutted by fire in close succession. This incident destroyed facilities worth millions of Naira but most importantly it was said that the value of the data/information destroyed could not be quantified in monetary terms (to describe the importance of the data destroyed).
From the above cases, without an effective backup system, the data will be lost for good and hundreds or even thousands of hours of work would’ve been lost.
The above are just two instances out of the many we hear on a daily bases.
ONLINE OFFSITE DATA BACKUP
Does your company still trust the backup of your most vital resource – data – to a fragmented and often ineffective policy of distributed USB disks, CDs, tape devices, manual routines, and manual offsite poorly planned storage? Or have you tried to use some “unlimited” consumer-based online backup solution, only to find that you cannot get your data back for a week (or never!) when the time comes that you need it? Lynxx Systems & Communication Technology LTD provides a business-class online offsite backup service that addresses the drawbacks of the fragmented USB disks, CDs, tape-based approach to backup with a unique service offering that is built specifically to handle the urgency of your business:
- Fully automated process with backups held on disk for rapid file restoration.
- Secure online transfer of fully encrypted data to an online offsite data center, ensuring regular backups are stored safely and remotely.
- Sound basis for business continuity planning – whatever happens, your data is safe.
- Cost-effective solution with an all-inclusive monthly service charge.
- 24 x 7 live customer support
- Immediate access to restore data when you need it
OFFLINE OFFSITE DATA BACKUP
Offsite Data Backup allows users to back up data to a remote, offsite location. This gives your organisation the ability to implement a data protection strategy that includes offsite storage of a backup of your data. This will require a well defined backup plan/schedule where we will be required to come at regular intervals and backup all your official data for offsite safekeeping. This will ensure that at any point in time you request for your data to be restored in an instance of any data disaster, giving you easy offsite data protection.
The option you choose will depend on first, the nature data + other conditions.
We are specialists, we definitely can HELP!!!
Adamu Fun Bala CSA; MD/CEO Lynxx Systems & Communication Technology LTD; 08035158065
Data Management – You ought to care – Part 2
- Creating the strategic link: Ask yourself why you need to do anything and what the expected value is. Identify the link between doing something and your corporate strategic objectives as defined within the company’s strategy.
- Deciding on scope and ambition level: Decide what is in scope to be governed. Is it local data and enterprise data? What role is data warehouse data playing? Which systems are involved?
- Identifying entities to be governed: Which data entities are in scope, i.e. customer, product, vendor, employee, etc.
- Modeling the entities: If you can’t model it, you can’t manage it. A prerequisite for defining the appropriate governance model is to design entities including the basic business definition, core minimum attributes, hierarchies, the life cycle and relevant classification.
- Identifying stakeholders: Who should be actively involved and why? Which roles are they likely to take, and how does it match the current organization in terms of their current positions and related power?
- Defining the data governance organizational model: Draw the governance model including all identified levels, roles and stakeholders from an enterprise level down to the local business units.
- Identifying and implementing changes in business processes: Document the new governance processes and how they either supplement or replace existing business processes.
- Communication, communication and communication: Constantly communicate the purpose and value of governance in order to change the culture toward adopting the new data governance organization and processes as a natural part of their every day duties and ways of working.
Data Management – You ought to care – Part 1
Caring is crucial in order to manage relationships as well as assets – we care about the things that matter to us. You know this from your private life. If you didn’t care about your most valuable assets, such as your kids, spouse, friends, car, boat or whatever they may be, it’s not hard to imagine what could happen: your kids would go totally out of control, your spouse and friends would leave you, your car would break down and your boat would sink. The same goes for any company/organisation – private or public – across any industry: we need to manage the things we care about, or to put it differently, we manage our assets.
So what are the important assets in your company? Most likely they are members, employees, products, buildings, capital, infrastructure, etc. These are all fairly tangible assets in the sense that we can hire and retire employees, we can buy and sell products, and we may invest in various markets and products and so on. We see dedicated ownership of all of these assets through various senior executives in finance, HR, IT, manufacturing and other business units. But who owns the data? If you, as many others do, consider data to be the product of your processes, data should be one of your most important assets, if not the most important. Additionally, data is one of our longest sustaining assets, since it was there yesterday and it will be there tomorrow. You don’t dispose of data that represents value to your business. People in the organization say they care about the data, but do they really? If caring means to focus, to be responsible and accountable, to define the one version of the data that meets the enterprise’s needs, then odds are nobody in your organization cares enough about data.